Thales SafeNet Trusted Access (STA)
Designing Flexibility to Enhance Enterprise Security
A UX deep dive into the Flexible Authentication feature for Thales's SafeNet Trusted Access (STA).
Overview
As a Sr. UX Designer for Thales's SafeNet Trusted Access (STA) platform, I led the end-to-end design for the Flexible Authentication feature. This enterprise solution tackles critical policy limitations by allowing administrators to configure primary and secondary (fallback) login methods. It eliminates frustrating lockouts for users with secure methods like FIDO or Certificate-Based Authentication (CBA), creating a more resilient and seamless login experience while encouraging the adoption of stronger security standards.
My Role
Sr. UX Designer (Lead)
Responsibilities
Research, UX Strategy, Prototyping, Usability Testing
Timeline
3 Months
The Problem: When Security Creates a Dead End
In the world of Identity and Access Management (IAM), stronger security is paramount. Our enterprise customers were increasingly adopting modern methods like FIDO security keys and Certificate-Based Authentication (CBA). However, the STA policy engine had a critical flaw: rigidity.
If a policy required a FIDO key, there was no alternative. An employee who forgot their key, a remote worker with a smart-card issue, or a user with an expired certificate was completely locked out. This created frustrating user dead ends, which led to:
- Increased Help Desk Costs: Every lockout resulted in a support ticket, increasing operational costs for our customers.
- Poor User Experience: Legitimate users were blocked from doing their work, causing frustration and reducing productivity.
- Hesitation to Adopt Security: The risk of locking out users made administrators hesitant to enforce the strongest authentication methods.
The Goal: Engineering Security Through Flexibility
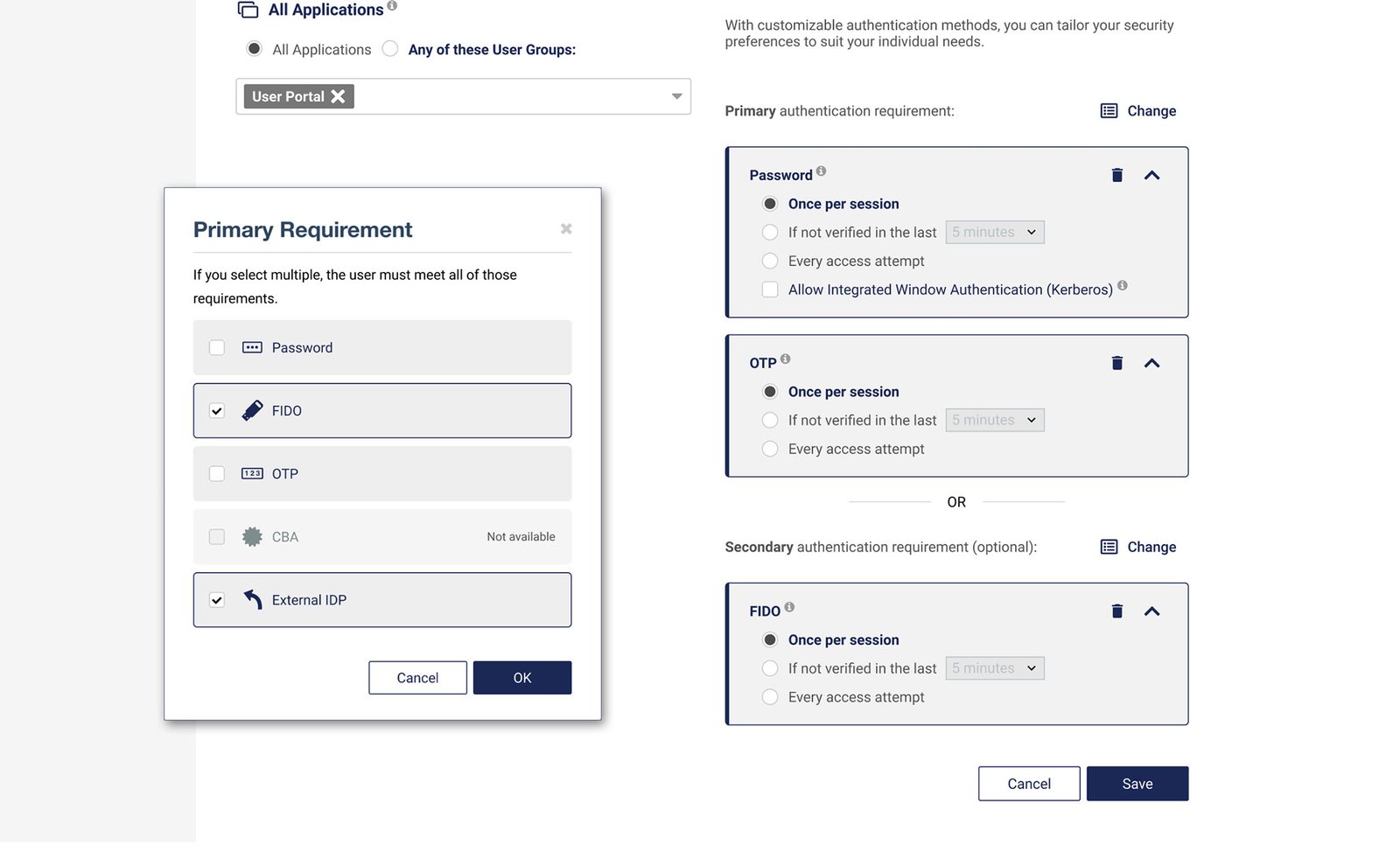
The project's objective was to dismantle this rigidity. We needed to design a system where an administrator could configure a primary login method while also offering secure alternatives. Our goals were to:
- Empower Administrators to build flexible yet secure authentication policies.
- Eliminate User Lockouts by providing intuitive fallback options.
- Drive Adoption of modern standards like FIDO and CBA by removing the primary adoption blocker.
- Deliver a Simple UX for both the technical administrator and the everyday end-user.
The Design Journey
Part 1: Discovering the End-User's Ideal Path
Before designing the administrator's experience, we had to solve the most critical question for the end-user: Should we default to the primary login method for speed, or present all choices upfront for clarity?

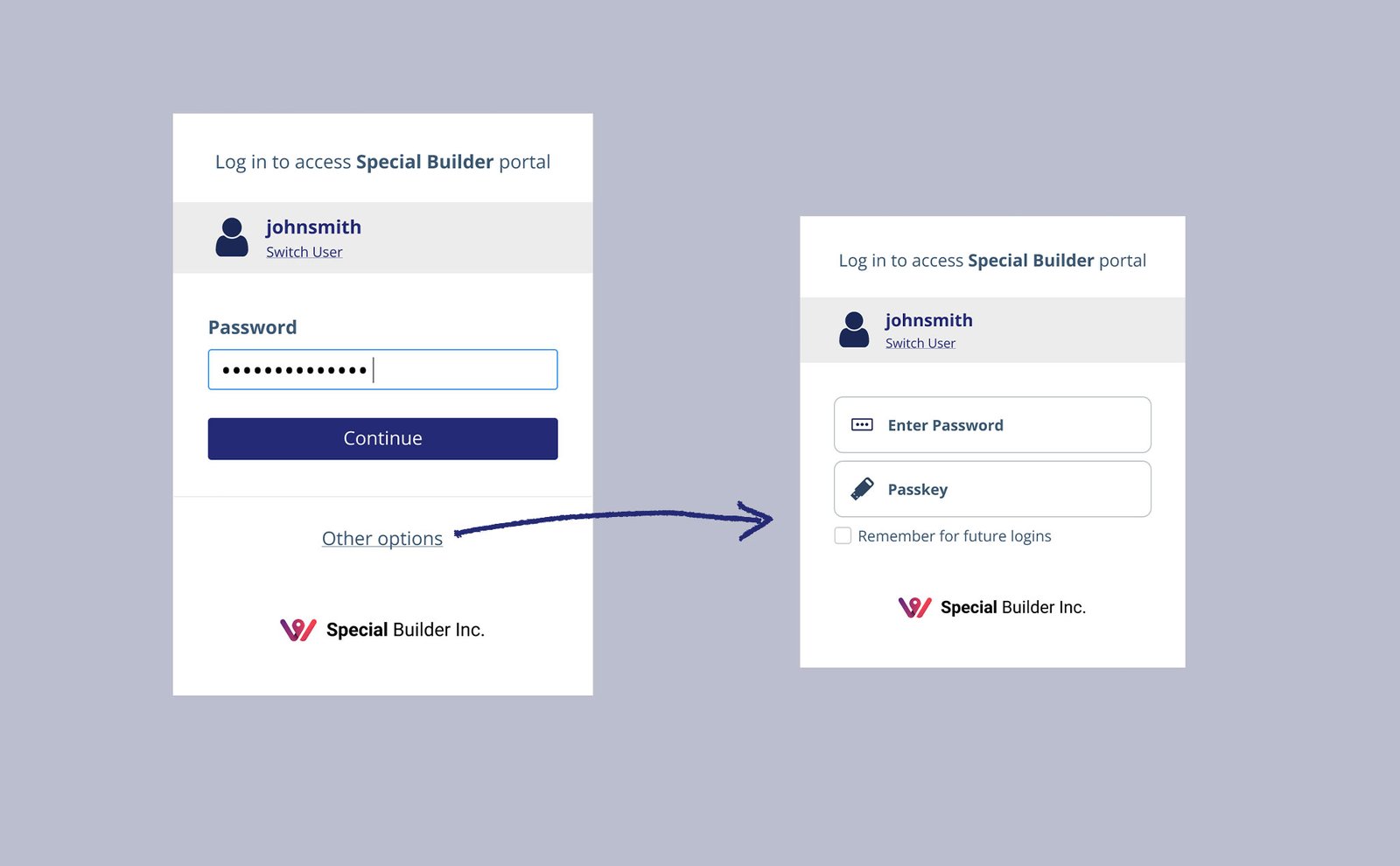
To get a data-driven answer, I led a remote usability study. The verdict was clear: Flow A, the "Default Path," offered the path of least resistance. It optimized for the most common use case while still providing easily discoverable flexibility.
Part 2: Empowering the Administrator
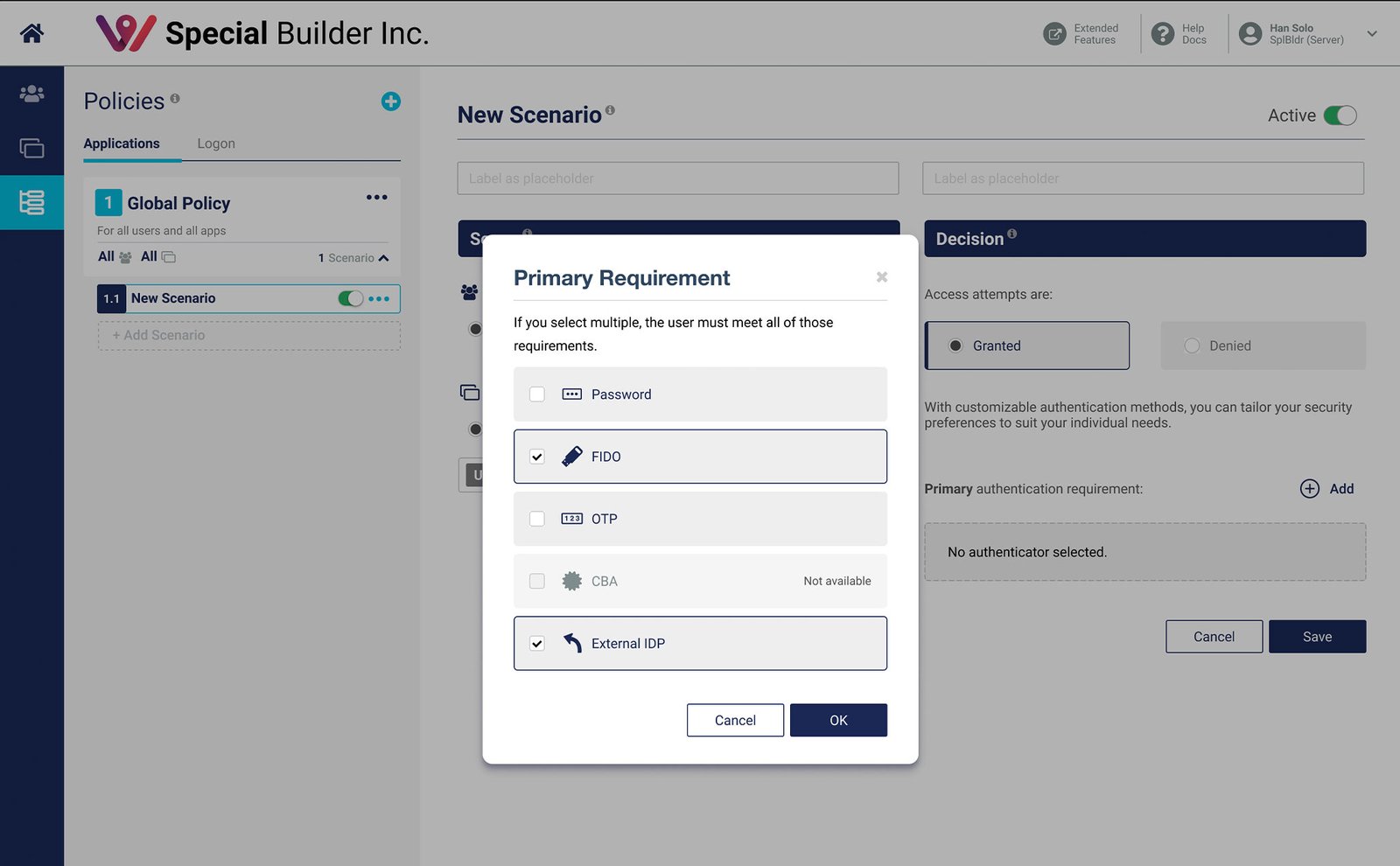
With a clear direction for the end-user, the focus shifted to the administrator. After weighing a complex drag-and-drop interface against a simpler modal selection pattern, we chose the modal approach for its consistency with our existing platform and faster development timeline.
A Key Decision: Prioritizing Feasibility and Consistency
Early in the administrator design process, we explored two distinct interaction models for configuring policies: a highly flexible Drag-and-Drop interface versus a simpler Modal Selection pattern. While drag-and-drop was interactive, we made a strategic decision to proceed with the modal approach for three key reasons:
- Consistency: The modal pattern was a well-established and tested component within our existing platform, ensuring the new feature would feel familiar.
- Feasibility: This approach was significantly less resource-intensive, allowing for faster development and alignment with our project timeline.
- Justified Simplicity: Our research indicated that administrators adjust these policies infrequently. The investment required for a novel drag-and-drop system couldn't be justified for a task performed so rarely.
I designed an interactive prototype of the chosen modal approach and validated it with experienced IAM administrators. The reception was overwhelmingly positive, with feedback like, "The complete flow was very clear. Everything was easy to use and setup."
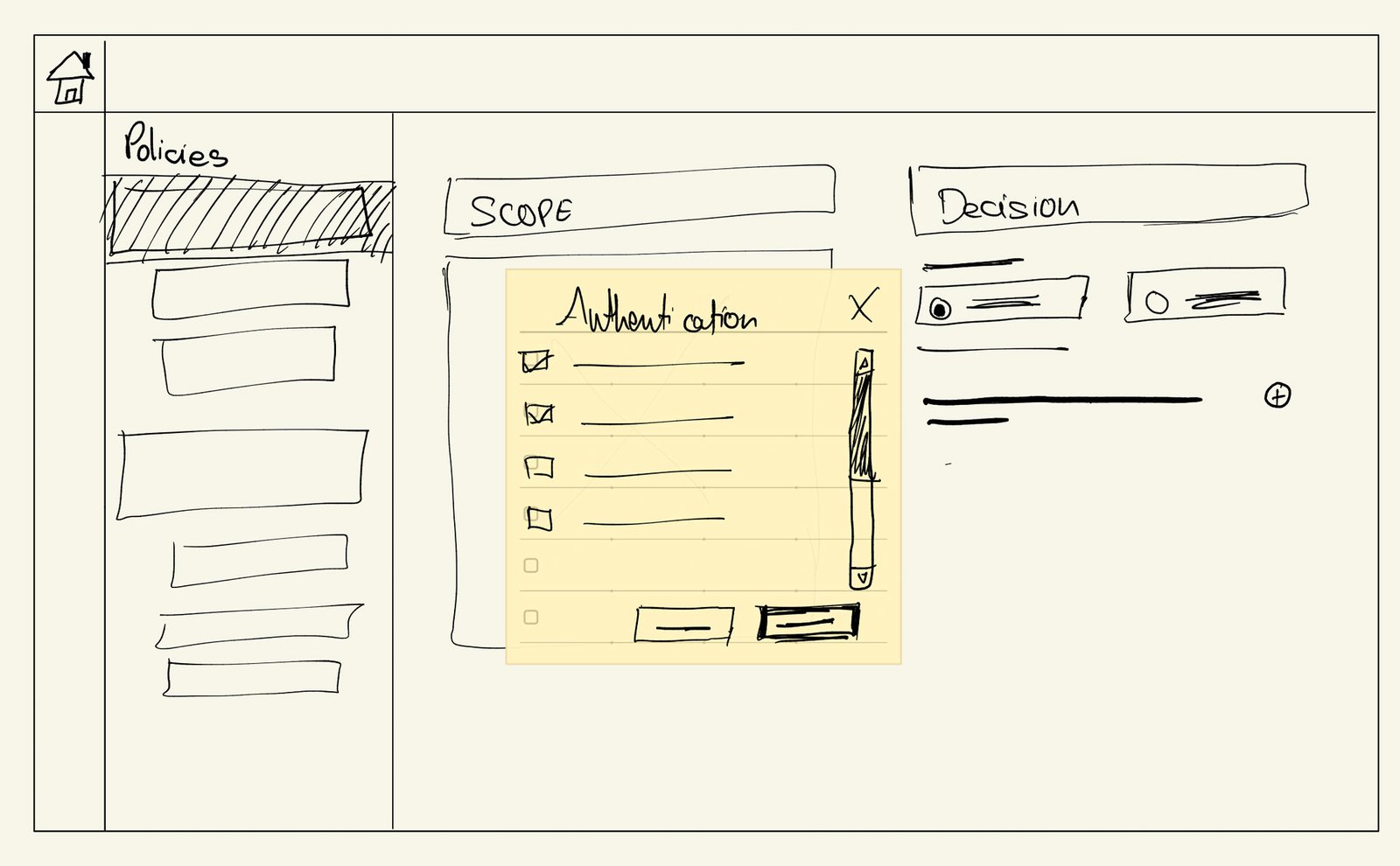
Part 3: From Insights to Pixels: Collaborative Refinement
The journey from research to final design involved close collaboration with product managers and engineers. We held several sessions to translate our findings into a polished, feasible product, making key decisions on balancing UX with business goals and perfecting the microcopy to be more instructional.
The Final Solution: A Unified Experience
The final design delivered a seamless experience that balanced the distinct needs of its two primary user groups.
The End-User Experience
We moved forward with the validated "Default Path" (Flow A). This provides the quickest login path for everyday use while the "Other options" link serves as an intuitive escape hatch for when things go wrong.
The Administrator Experience
The final admin console provides a clean, two-step process for building policies. It uses progressive disclosure to reveal secondary options only after the primary is set, and smart UI constraints prevent invalid configurations.
Impact & The Road Ahead
The Flexible Authentication feature was successfully released and the initial feedback from key customers was overwhelmingly positive. One of our enterprise customer reported that they were "very happy with the feature," a direct validation that we solved a critical real-world problem.
The release also opened a new channel for user feedback, which has been crucial for shaping the product roadmap and underscores our commitment to continuous, user-centered improvement.
Personal Reflection
This project was a masterclass in balancing the needs of two very different user groups: the highly technical administrator and the non-technical end-user. The success of the feature hinged on our commitment to pre-launch validation. The insights gained from our usability tests allowed us to move into development with a high degree of confidence and, ultimately, deliver a solution that was powerful, intuitive, and impactful.